Electronics | Free Full-Text | Detection of Vulnerabilities in Smart Buildings Using the Shodan Tool

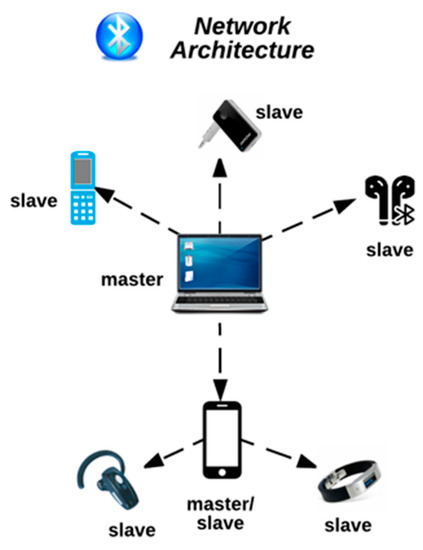
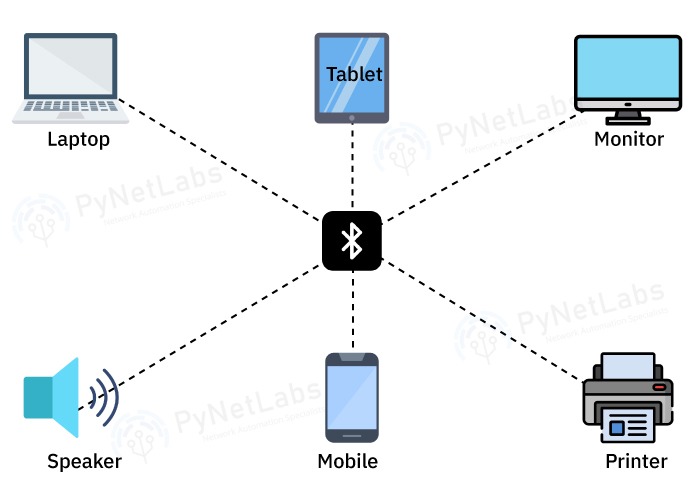
Hackind_tech on Instagram: "⚠️Diving into the world of Bluetooth security: ever heard of bluebugging, bluesnarfing, BTCrack, and Btlejack📱📡🔒🔥 Exploring the intricacies of digital landscapes and staying curious. 🔍💡 👉 Bluing:This term is











)