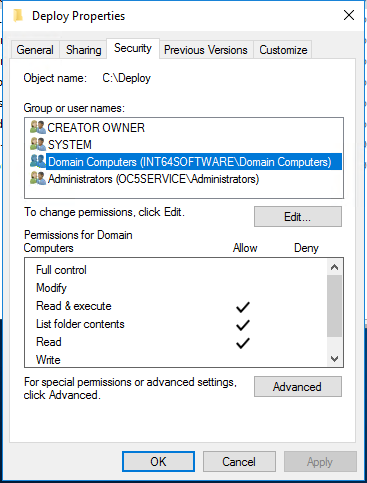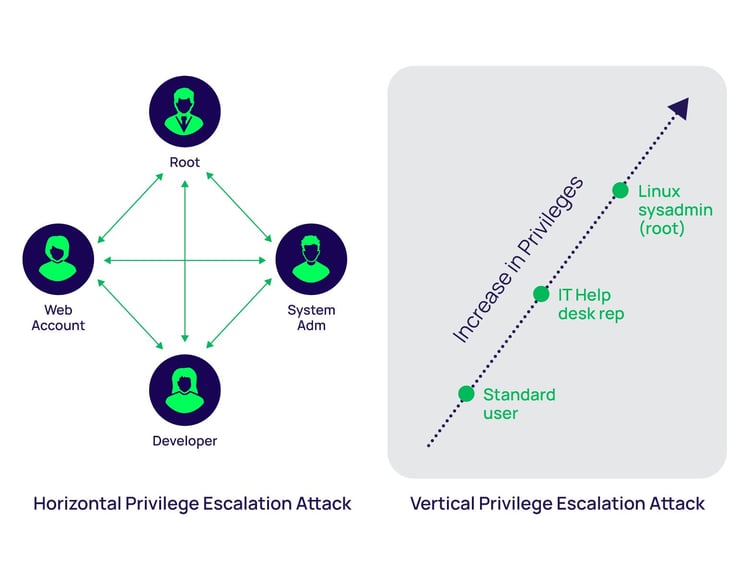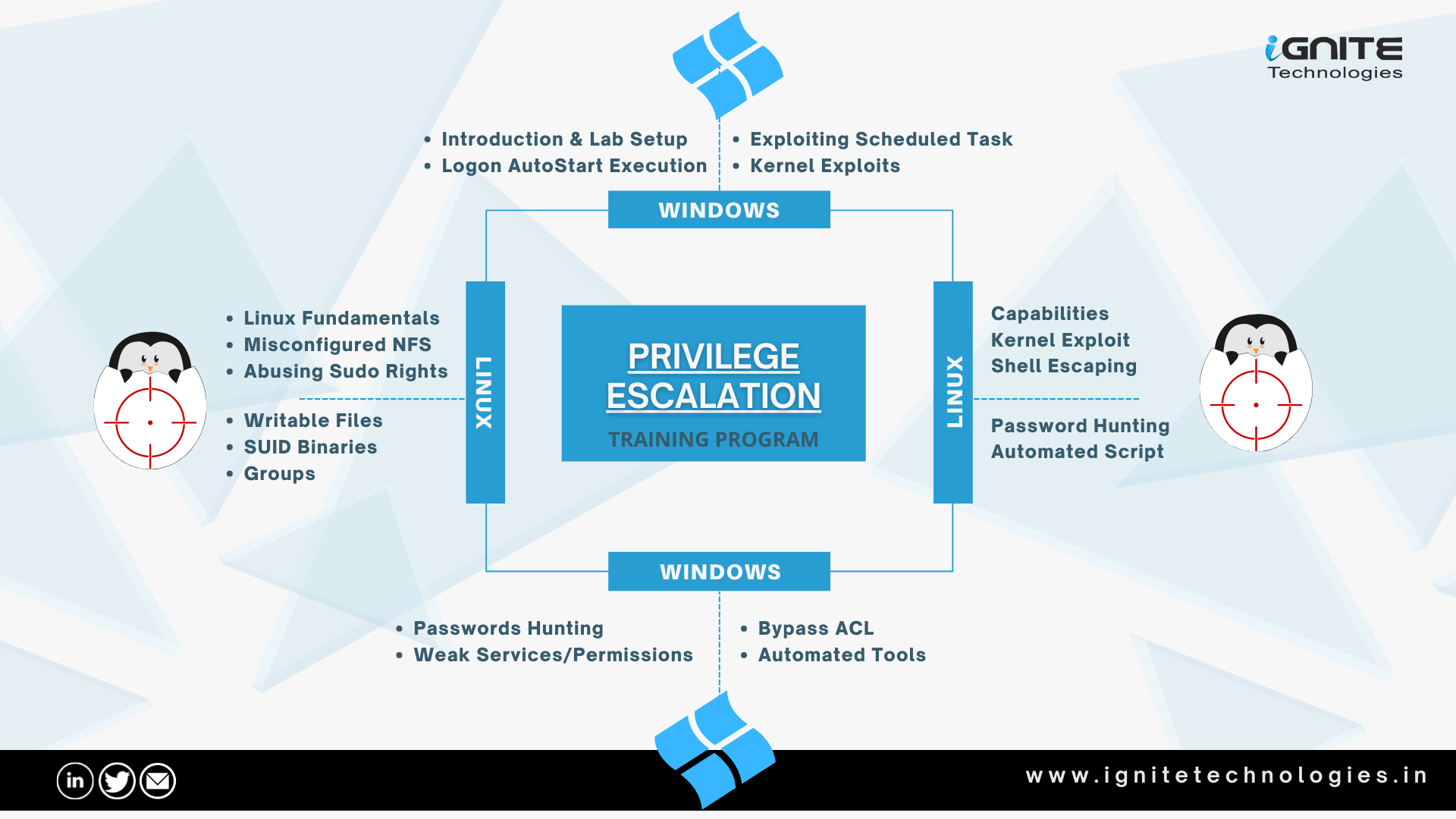
GitHub - Ignitetechnologies/Linux-Privilege-Escalation: This cheatsheet is aimed at the OSCP aspirants to help them understand the various methods of Escalating Privilege on Linux based Machines and CTFs with examples.

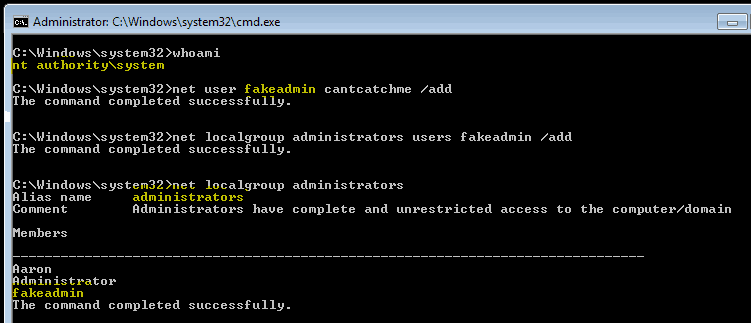
Windows privilege escalation via Misconfigured Services, Registry, SAM/SYSTEM files, User Impersonation | by n00🔑 | Medium